Welcome to the last part of InSpec and Chef Compliance for Windows infrastructure testing. In this last article you will see how Chef Compliance adds value to your infrastructure and how to use your new shiny profile against your Windows machines.
Let´s start with the easy thing: adding a node to compliance. Since the profile is now centrally available on your Chef Compliance server you´re able to add another Windows node or your Test-Kitchen VM using the public IP address and a WinRM user/password. If you don´t know the IP address yet you can just run
kitchen login
to connect to your VM and determine the IP address using the “ipconfig” command on the shell.
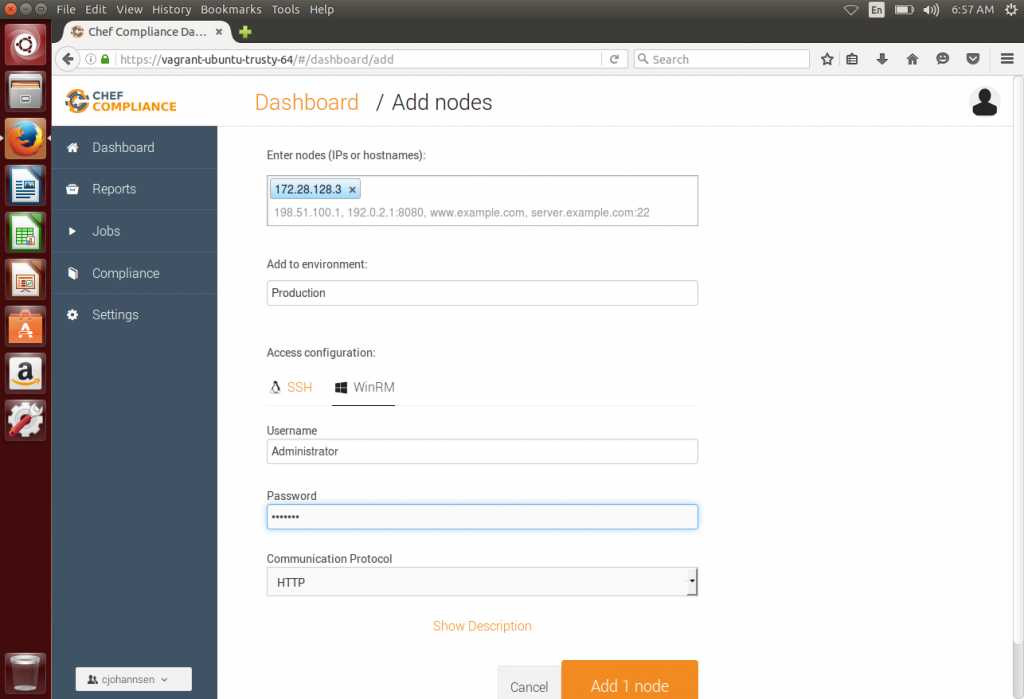
Now enter the Chef Compliance portal again and click “Dashboard” and then “Add Nodes”. Now you can add your node, using the IP or hostname, naming a new environment and enter username and password. Then click “Add 1 Node”.
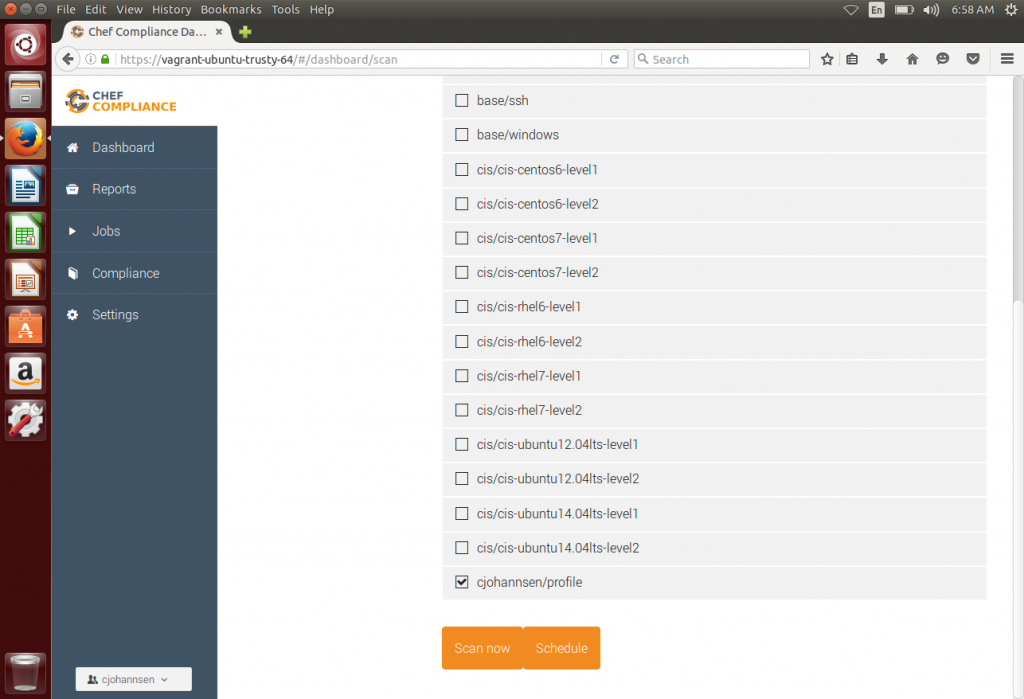
Now select your new node and click “Connectivity” to verify that the node is reachable. As soon as this succeeds you can now go back to your dashboard, select an environment or node and click the “Scan” button. With Chef Compliance there are different profiles already shipped. Please unselect all scans and just check your example profile. Then click “Scan Now” to start the test against your node.
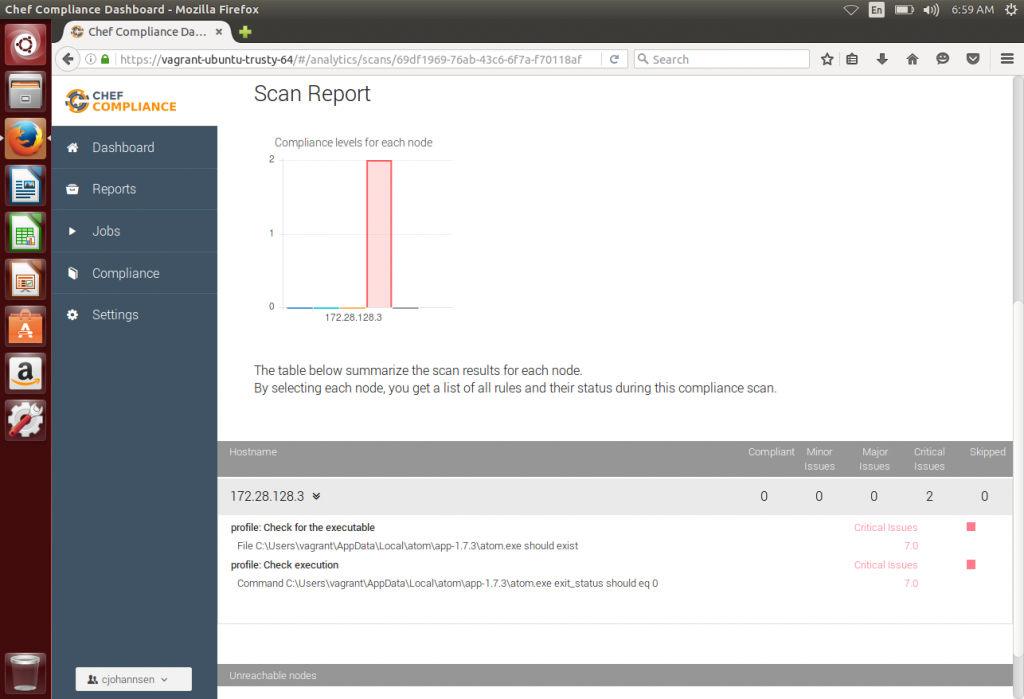
After the scan is done there should be a compliance report visible that shows the result of your controls within the profile.
Since my Test-Kitchen VM was destroyed and there was no converge, the report shows critical issues based on our profile. With a simple:
kitchen converge
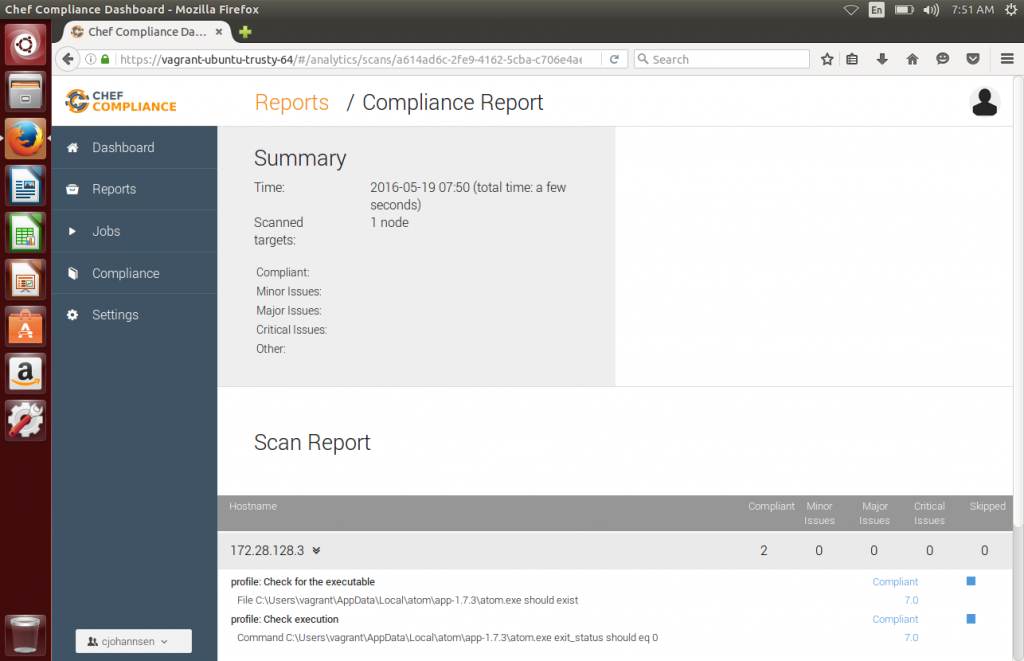
it now has the “Atom” cookbook applied and the new run shows that everything is okay:
So far you installed ChefDK, generated a cookbook, used InSpec to write tests, configured Test-Kitchen to use InSpec, wrote controls and created a profile for Chef Compliance. You also used the cookbook to do a re-imediation after your Chef Compliance scan showed critical errors.
But there is one more thing: A so called audit-cookbook that can be run while you´re using your cookbooks.
The preferred usage of the compliance cookbook is to upload it to your Chef Server and add it to the run-list of your client, with setting the attribute of the profile that should be used. After you uploaded the audit cookbook to your Chef Server:
knife cookbook upload audit
it becomes generally available.
When you add this cookbook to an existing run_list of a node or your test-kitchen you can set the profile to call as an attribute:
default['audit']['profiles']['cjohannsen/profile'] = true
That should be enough to call your profile while you´re running having a chef-client run or a test-kitchen converge run.
In the next part I will shed some light on the last part: How to use Chef Compliance and the audit-cookbook without a Chef Server!